Understand the difference between IPv4 and IPv6 addresses:
What is IPv4?
IPv4 (Internet Protocol version 4) is the fourth version of the Internet Protocol. It is the most widely used protocol for routing traffic on the internet and supports about 4.3 billion unique IP addresses, which is achieved through a 32-bit address space. IPv4 addresses are typically written in decimal as four numbers separated by dots (e.g., 192.168.1.1).
What is IPv6?
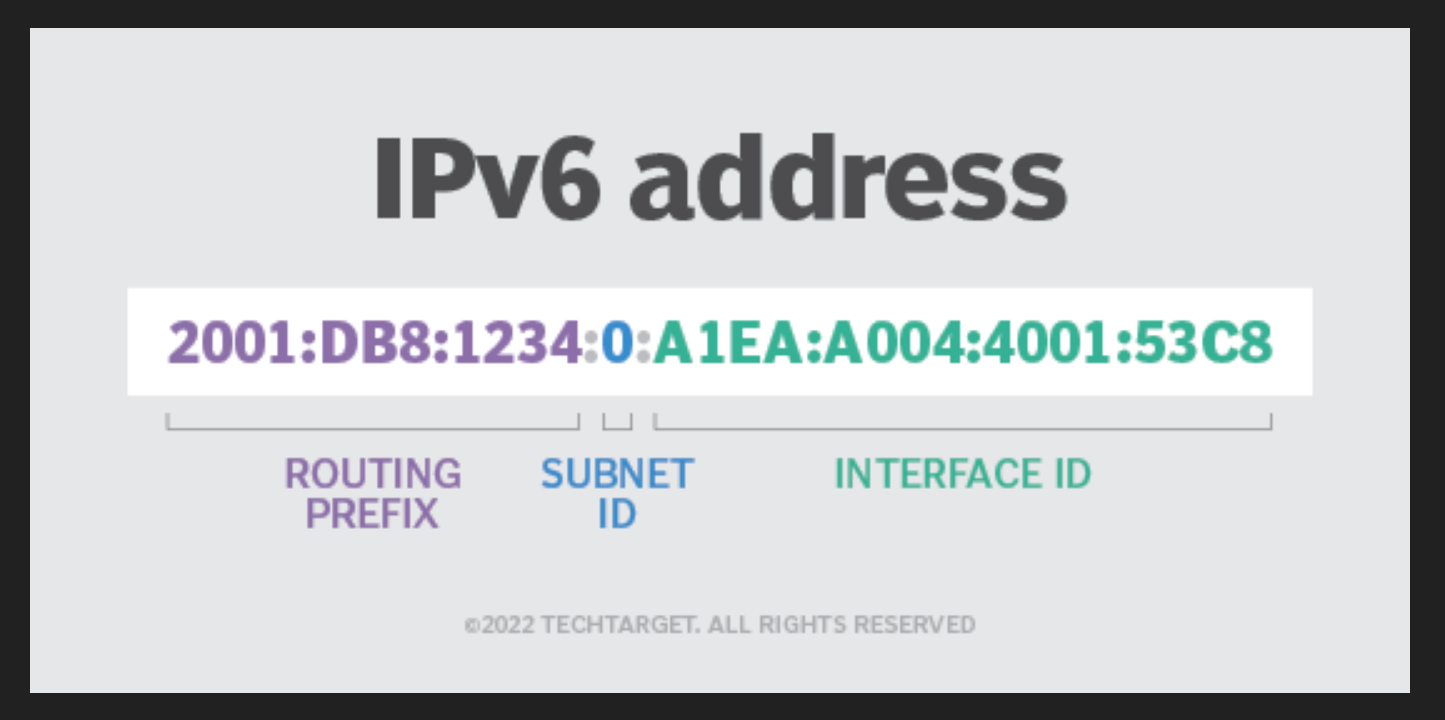
IPv6 (Internet Protocol version 6) is the successor to IPv4 and was developed to address the limitations of IPv4, primarily the exhaustion of available addresses. IPv6 uses a 128-bit address space, allowing for a virtually limitless number of unique IP addresses (approximately 340 undecillion addresses). IPv6 addresses are written in hexadecimal and separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
So 4.3 billion possible addresses vs effectively endless addresses… but IPv4 is preferred from a privacy standpoint.
Key reasons why IPv6 is detrimental to user privacy:
- Predictable Addressing:
- Stable IPv6 Addresses: IPv6 addresses can often be derived from a device’s MAC address, leading to stable, predictable IP addresses. This predictability allows for easier tracking of devices over time and across different networks, as the same address may be reused.
- Increased Exposure:
- Direct Connectivity: IPv6 was designed for end-to-end connectivity, which reduces the need for NAT (Network Address Translation). While this can improve performance, it also means devices are more directly accessible on the internet, potentially increasing the risk of exposure to tracking and data collection.
- Less Anonymity:
- Linkability: Since IPv6 addresses can remain the same across different networks (unless privacy extensions are used), they can be linked to specific devices or users, reducing anonymity and making it easier for third parties to track user behavior.
- Privacy Extensions Not Widely Adopted:
- Lack of Default Use: IPv6 includes Privacy Extensions (RFC 4941) that generate temporary addresses to enhance privacy. However, not all operating systems and devices enable these extensions by default, leaving users vulnerable to tracking.
- Misconfiguration Risks:
- Improper Implementation: Many networks and devices still primarily use IPv4 and may have poorly configured IPv6 settings. This can lead to scenarios where IPv6 traffic is unprotected or routed in a way that exposes user data.
- Enhanced Tracking Capabilities:
- Increased Data Collection: With the proliferation of IoT devices and the vast address space of IPv6, more devices are online, potentially increasing the amount of data that can be collected and analyzed by advertisers and other third parties.
- Complexity in Privacy Management:
- Difficulty in Control: Managing privacy in an IPv6 environment can be more complex due to the sheer number of addresses and devices. Users may find it challenging to maintain privacy settings consistently across multiple devices and applications.
How and where can you disable IPv6 on your systems?
We can disable IPv6 in a number of ways, primarily at the following levels:
System Firewall
Router
Managed Switches
Computer/Device (operating system)
Applications (such as your browser)
While there are too many options to cover IPv6 disabling on all Network Routers, Firewalls and Switches, we can search through the settings on these device dashboards (usually you access these dashboards with an IP address that is printed on the bottom of your device).
In addition, here we will cover how to disable IPv6 at the Operating System level (on your computer) with Linux. This applies to most Debian based Linux systems including our preferred Pop!_OS, we will be using the terminal to enter the commands below. (or skip to the bottom of this page if you want to cheat and run a script that does this for you instead)
First, open a terminal and update your machine by running:
sudo apt update && sudo apt upgrade -y
Now let’s modify iptables, run the following commands:
sudo apt install iptables-persistent
sudo ip6tables -P INPUT DROP
sudo ip6tables -P FORWARD DROP
sudo ip6tables-save | sudo tee /etc/iptables/rules.v6
Next, let’s modify the configuration file /etc/sysctl.conf by adding the following lines within the configuration file:
sudo nano /etc/sysctl.conf
Copy and paste the following lines towards the bottom anywhere in sysctl.conf:
net.ipv6.conf.all.disable_ipv6 = 1 net.ipv6.conf.default.disable_ipv6 = 1 net.ipv6.conf.lo.disable_ipv6 = 1
Hit Ctl+O and Enter to save, Ctl+X to exit.
Next let’s modify a similar file located at /etc/ufw/sysctl.conf:
sudo nano /etc/ufw/sysctl.conf
Comment out the following lines (add a # symbol) in front of these lines:
#net/ipv6/conf/all/accept_redirects=0 #net/ipv6/conf/default/accept_redirects=0
net/ipv6/conf/default/autoconf=1 net/ipv6/conf/all/autoconf=1
sudo nano /etc/default/grub Look for the line: GRUB_CMDLINE_LINUX="" and modify it to this: GRUB_CMDLINE_LINUX="ipv6.disable=1"
sudo update-grub sudo reboot (Reboots your entire machine)
sudo nano /etc/NetworkManager/NetworkManager.conf
[ifupdown] managed=true
[ipv6]
method=ignore
sudo systemctl restart NetworkManager
Disabling IPv6 in avahi (some distros)
sudo nano /etc/avahi/avahi-daemon.conf
use-ipv4=yes use-ipv6=no